Knowledge base
1000 FAQs, 500 tutorials and explanatory videos. Here, there are only solutions!
This guide explains the main differences between an EV and a DV certificate.
EV SSL Certificates: for companies
The Sectigo EV SSL certificate can only be issued to companies registered in an official registry.
It provides the highest level of trust with your customers and offers unique benefits in addition to including the benefits of a DV certificate:
Your company name in thenavigation bar- padlock in the navigation bar
- dynamic secure site seal
- validation of your domain name
- manual authentication of your company's contact details and identity
- guarantee up to $1,750,000 for end users
- 7/7 support
Activating an EV SSL certificate can take up to 24 hours and will require actions on your part.
DV SSL Certificates: for companies and individuals
The Sectigo DV certificate is open to individuals and companies. It does not include some of the benefits mentioned above, but it offers additional benefits over free Let's Encrypt SSL certificates:
- dynamic secure site seal
- validation of your domain name
- guarantee up to $10,000 for end users
- 7/7 support
Activation of a DV SSL certificate is immediate.
And the Let's Encrypt certificates?
A free Let's Encrypt certificate guarantees the same level of encryption as an EV or DV certificate. However, Let's Encrypt certificates do not offer the following benefits:
- manual validation of your company's contact details and authenticity (EV)
- guarantee for end users in case of fraud (EV/DV)
- support in case of questions
In summary, Let's Encrypt certificates ensure the encryption of exchanges between your users and your site, but they do not guarantee to internet users that they are on a legitimate site whose identity has been authenticated by a certification authority.
This guide suggests solutions to resolve common issues and frequent errors that may occur when you try to display your website in https after activating an SSL certificate.
The web browser automatically displays the http version of the site when you try to access it in https
It is recommended to perform the following actions:
- Empty the cache of your applications or your site.
- Check that the pages and scripts of the site do not contain redirects to the
httpversion of the site. - Check that the site's
.htaccessfile does not contain redirects to thehttpversion of the site. - Set the site's
httpsaddress as the default one:
The website is displayed incorrectly (missing images, unsupported stylesheets, etc.) or displays a warning in the address bar
It is recommended to perform the following actions:
- Empty the cache of your applications or your site.
- Check that the pages and scripts do not point to external resources in
http; the site whynopadlock.com can help you identify the unsecured elements of your site. - Also refer to this other guide on this subject.
"This web page has a redirect loop", "ERR_TOO_MANY_REDIRECTS"
If your web browser displays this error, it is recommended to perform the following actions:
- If the site works with a web application like WordPress or Joomla, deactivate the extensions one by one to identify the problematic one.
- Check that the pages and scripts of the site do not contain redirects to the http version of the site.
- Try to deactivate HSTS.
- If Prestashop is used, SSL must be activated on all pages:
- Add your SSL domain:
- Go to Preferences > SEO & URLs.
- In the "Store URL" section, enter your site address in the "SSL Domain" field (without the
https://, justwww.domain.xyz).
- Activate SSL:
- Go to Preferences > General settings.
- At the top of the page, click on "Click here to use the HTTPS protocol before activating SSL mode."
- A new page will open with your site in the secure HTTPS version.
- Force the use of SSL on the entire site:
- Go back to Preferences > General settings.
- Set the "Enable SSL" option to YES.
- Also set "Force the use of SSL for all pages" to YES.
- Add your SSL domain:
An old SSL certificate is displayed - clear the SSL cache
Web browsers cache SSL certificates to speed up navigation. Normally, this is not a problem. However, when you develop pages for your website or install a new certificate, the browser's SSL status may bother you. For example, you might not see the padlock icon in the browser's address bar after installing a new SSL certificate.
The first thing to do in this case is to make sure that the domain points to the server's IP address (A and AAAA records) and if it is still the wrong SSL certificate that is returned, clear the SSL cache:
- Chrome: go to Settings and click on Settings. Click on Show advanced settings. Under Network, click on Change proxy settings. The Internet Properties dialog box appears. Click on the Content tab. Click on Clear SSL state, then click OK. Refer to other tips in this other guide.
- Firefox: go to History. Click on Clear Recent History then select Active Connections and click on Clear Now.
Loss of CSS formatting
If the website is displayed without CSS style, analyze the page loading with the browser Console. There may be mixed content errors (mixed content) related to your styles .css, which you will need to resolve so that they are loaded correctly again.
Cloudflare
If you are using Cloudflare, refer to this other guide on the subject.
Thank you for choosing Infomaniak to secure your sites with an EV or DV SSL certificate from Sectigo.
An SSL certificate secures all exchanges between your server and your visitors, displays a padlock, and adds the https to your site.
Main SSL guides
- Order a Sectigo EV SSL certificate
- Understand the difference between EV and DV certificates
- Use a Sectigo certificate on an external site (other host)
- Understand the Sectigo guarantee for SSL certificates
- Resolve an SSL/https issue
- Install a free Let's Encrypt SSL certificate on a site
- Install a free 'wildcard' SSL certificate
- Uninstall an SSL certificate
- Update a Let's Encrypt SSL certificate (for example, after adding/removing aliases)
Additional help
- Find out about all the SSL FAQs
- Contact Infomaniak support
This guide helps you diagnose and resolve the error "Your connection is not private" (or NET::ERR_CERT_AUTHORITY_INVALID). This security alert can affect both visitors to a site and its administrators.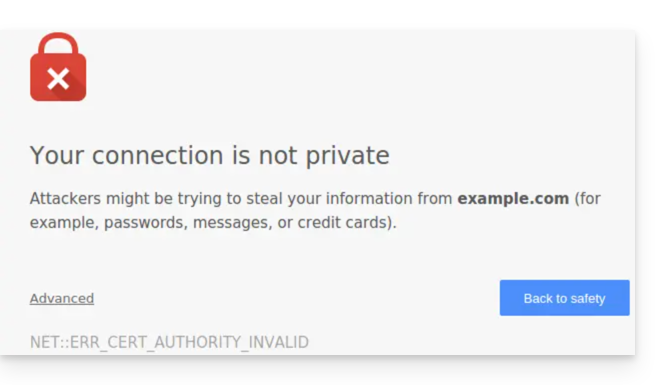
Preamble
- This alert is a protection mechanism of your browser. It indicates that a secure connection could not be established with the server for one of the following reasons:
- The site does not have an SSL/TLS security certificate.
- The installed certificate is expired or misconfigured.
- The connection between your device and the server is intercepted or disrupted.
- Warning: On a site showing this error, the data you enter (passwords, card numbers) are not encrypted and can be intercepted by third parties.
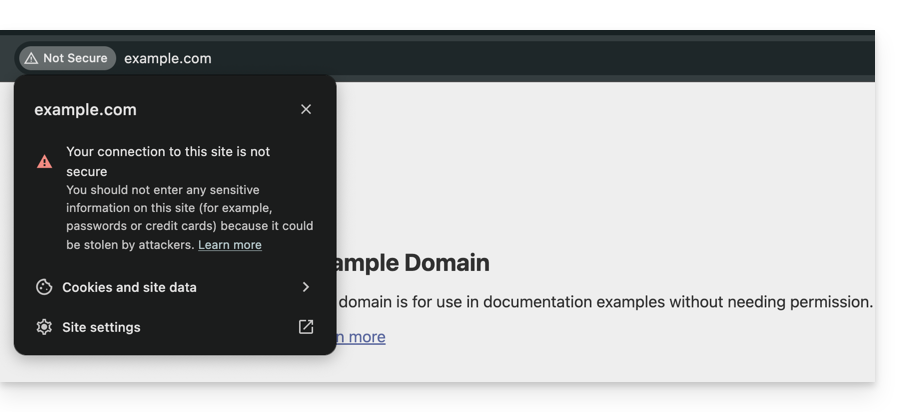
Solutions for visitors
If you encounter this error on a site you do not manage, the problem may sometimes come from your own configuration. Here are the points to check:
- Check the time on your device: If your computer or smartphone is not at the correct date/time, the certificate validation will systematically fail.
- Test in private browsing: If the error disappears, clear the cache and cookies of your browser.
- Check your network: Avoid public Wi-Fi networks that may force their own login portals.
- Antivirus and Firewall: Some security software analyze HTTPS connections and can cause false positives.
Solutions for Infomaniak site owners
If you are the site administrator, you must ensure that your SSL certificate is active and valid to cover all of your domain names.
1. Is the SSL certificate installed?
If your site is still in HTTP, you need to generate a certificate (free via Let's Encrypt or paid). Learn about the certificates available at Infomaniak.
Important: If you have added aliases (secondary domain names) to your site after installing SSL, you must update the certificate to include them.
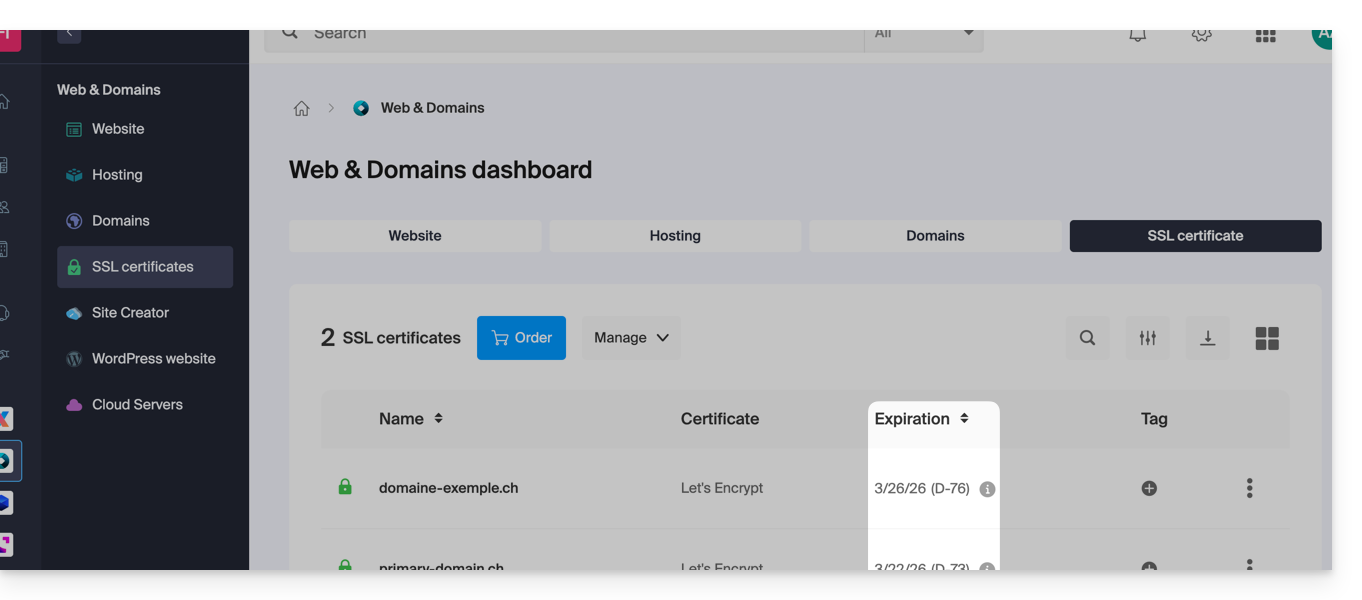
2. Check validity and expiration
At Infomaniak, certificates are renewed automatically, but a technical issue may sometimes occur. To check the status of your certificate:
- Click here to access the management of your certificates in the Manager (need help?).
- Check the status and expiration date in the dashboard:
3. Force HTTPS and fix the "Mixed Content"
If your certificate is valid but the error persists (or the padlock is not green), it is possible that your site is still loading elements (images, scripts) in HTTP. To fix this, refer to this other guide.
This guide explains how to install a free SSL certificate from Let's Encrypt on a website hosted by Infomaniak.
Preamble
- Once the certificate is installed, your website will be accessible in
httpandhttps… - If you want to include an alias domain name recently added to your site that already had a certificate, you need to update it.
- For multiple subdomains, refer to this other guide.
- Let's Encrypt limits the installation of certificates to:
- 100 subdomains
- 20 certificates for 7 days per registered domain
- 5 unsuccessful requests per account per hostname per hour
Install a free SSL certificate on a site
Prerequisites
- For the installation to be possible, the DNS of the domain name must be correctly configured to point to the site in question.
- If a change has just been made at this level, some operations may not be functional immediately.
To access websites to install an SSL certificate:
- Click here to access the management of your product on the Infomaniak Manager (need help?).
- Click directly on the name assigned to the product in question:
- Click on Configure under SSL Certificate:
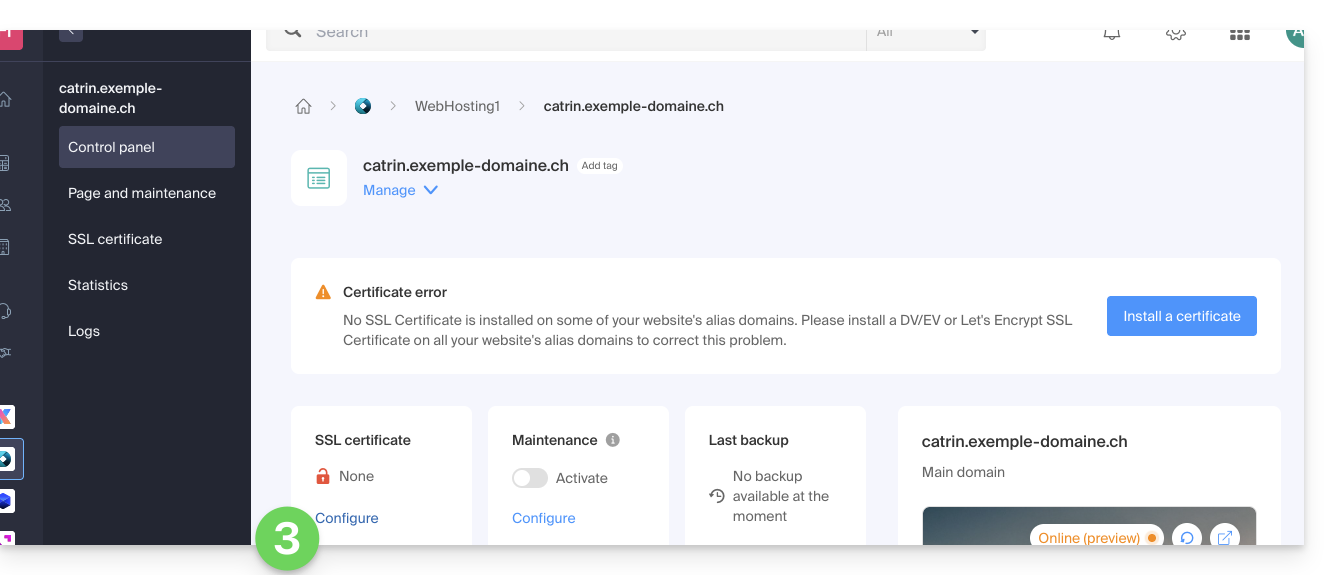
- Click on the Install a certificate button:
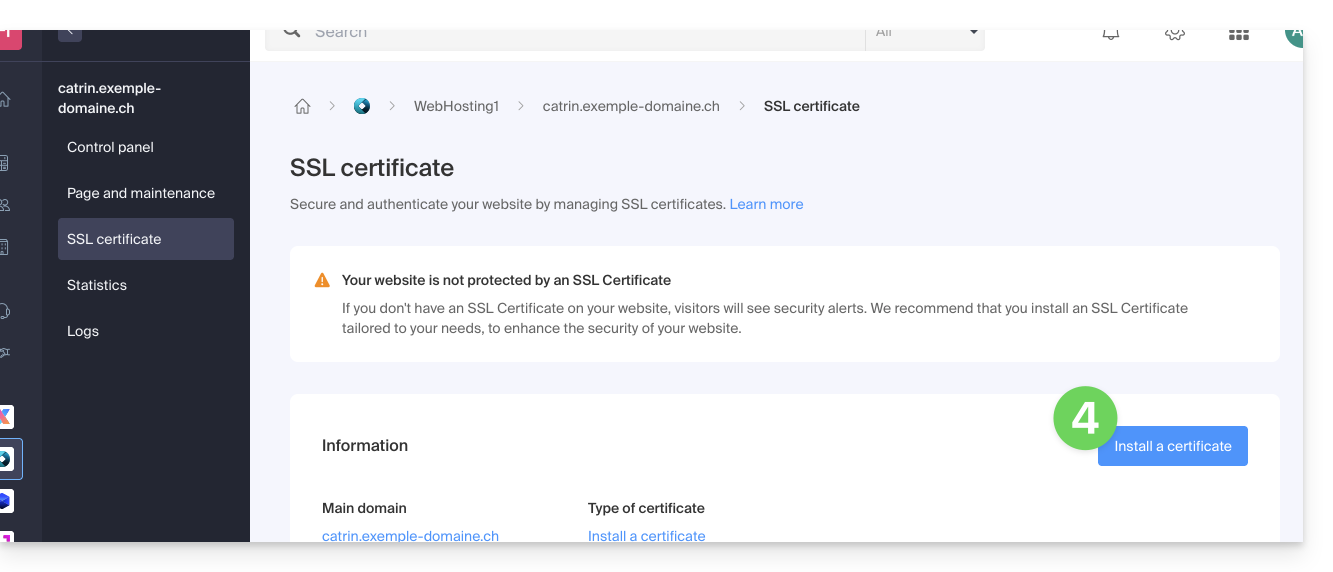
- Choose the free certificate.
- Click on the Next button:
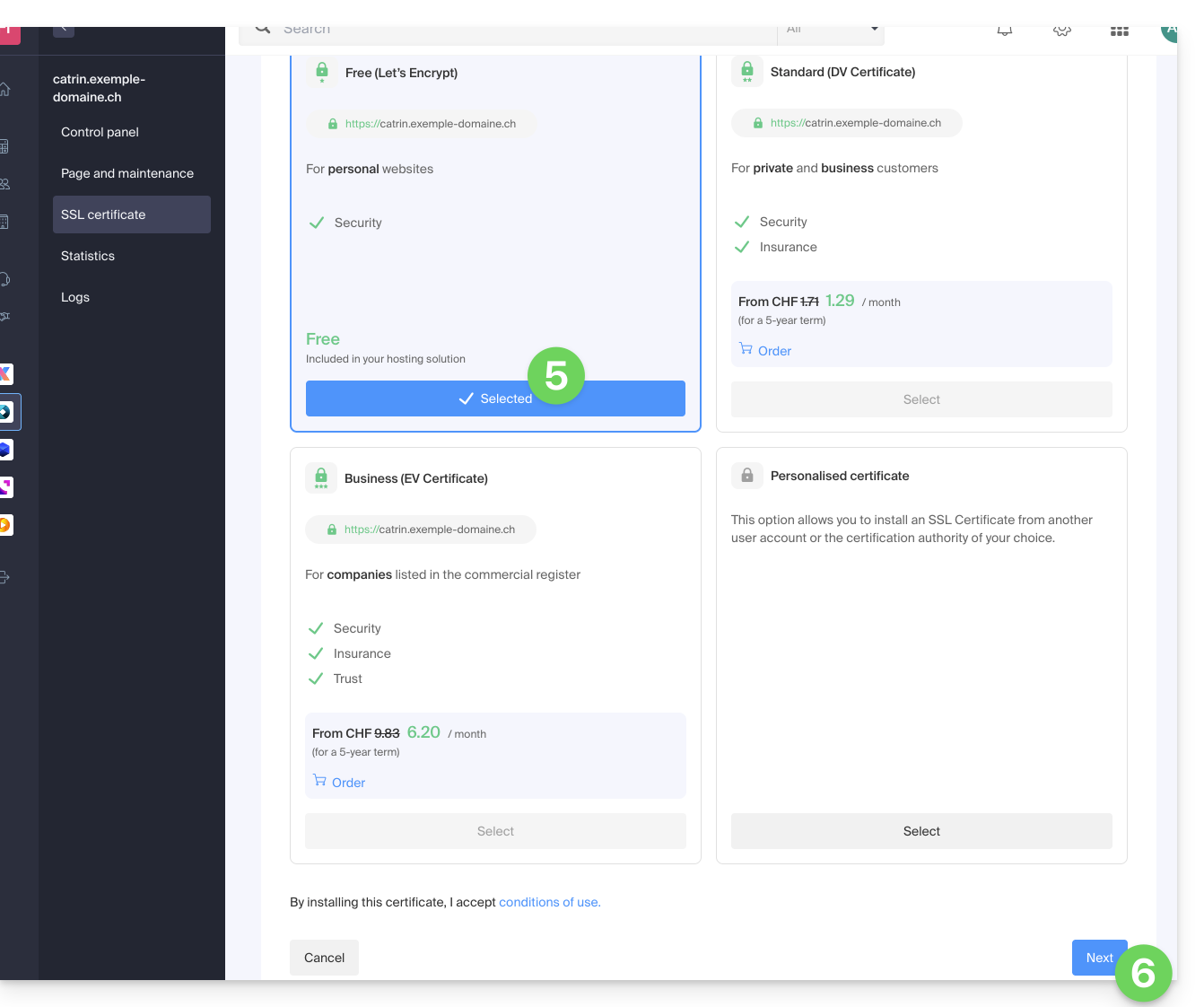
- Check or select the domains concerned.
- Click on the Install button:
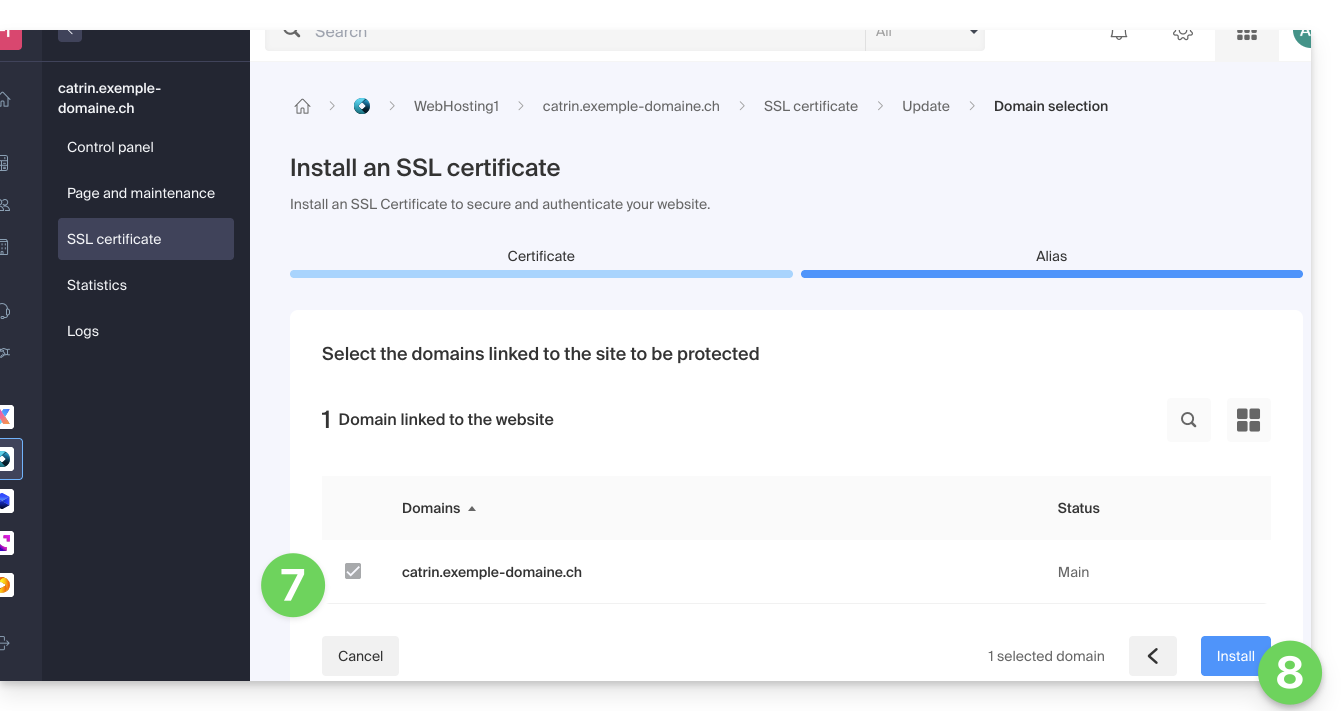
- Wait a few minutes until the certificate is obtained on the site.
Refer to this guide if you encounter SSL errors and to this other guide specifically if you are using Cloudflare.
This guide explains how to generate and then automatically renew a wildcard certificate via DNS challenge using Certbot and the dns-infomaniak plugin.
1. Installing the Infomaniak DNS plugin
DNS plugins are not installed by default with Certbot. To correctly install certbot and the dns-infomaniak plugin, to avoid a possible error The requested dns-infomaniak plugin does not appear to be installed, refer to the official Certbot instructions and choose the correct Software → System and then consult the Wildcard tab.
2. Generate the wildcard certificate
From a Terminal, run the following Certbot command to manually generate the certificate:
certbot certonly --manual \
-d *.domain.tld \
--preferred-challenges dns-01 \
--server https://acme-v02.api.letsencrypt.org/directory3. Create the TXT record
From the domain management of the Infomaniak Manager, create the requested TXT record for _acme_challenge.domain.tld.
4. Create the renewal configuration file
From a Terminal, create or edit the file: /etc/letsencrypt/renewal/domain.tld.conf. Example of recommended configuration:
cert = /etc/letsencrypt/live/domain.tld/cert.pem
privkey = /etc/letsencrypt/live/domain.tld/privkey.pem
chain = /etc/letsencrypt/live/domain.tld/chain.pem
fullchain = /etc/letsencrypt/live/domain.tld/fullchain.pem
[renewalparams]
authenticator = manual
manual_auth_hook = /root/infomaniak-auth.sh
manual_cleanup_hook = /root/infomaniak-clean.sh
server = https://acme-v02.api.letsencrypt.org/directory
pref_challs = dns-01
account = xxxxx
key_type = rsaSome errors come from files automatically generated by Certbot containing obsolete or incorrect fields (version = ..., cert-path = ..., etc.). Always recreate the renewal file following the example above.
5. Create the infomaniak-auth.sh script
From the API management of the Infomaniak Manager, create an Infomaniak API token with the domain scope, which will replace XXXXXXX in the script below.
The file indicated in your configuration must absolutely match the real name of the script. Example: if you use infomaniak-auth.sh in the configuration, do not create infomaniak-auth-domain.xyz.sh.
From a Terminal, create the file /root/infomaniak-auth.sh without trailing tabs (they cause errors in Bash) with:
#!/bin/bash
INFOMANIAK_API_TOKEN="XXXXXXX"
# Ajout de l'enregistrement TXT via le plugin DNS Infomaniak
/usr/bin/certbot \
--authenticator dns-infomaniak \
--server https://acme-v02.api.letsencrypt.org/directory \
-d "$CERTBOT_DOMAIN" \
--agree-tosThe script must be made executable:
chmod +x /root/infomaniak-auth.sh6. Create a cleanup script
Create the file /root/infomaniak-clean.sh
#!/bin/bash
# Optionnel : suppression de l'entrée DNS temporaire
exit 0The script must be made executable:
chmod +x /root/infomaniak-clean.sh7. Test the renewal
Before using a cron, always test with this command that will display any potential errors (script not found, incorrect file name, missing permissions, missing plugin, etc.):
certbot renew --dry-run8. Configure a cron task
0 0 */30 * * /usr/bin/certbot renew --quiet --config /etc/letsencrypt/renewal/domain.tld.confModify 30 days above according to the desired frequency. The cron will automatically use:
- the file
domain.tld.conf - the authentication script
infomaniak-auth.sh - the plugin
dns-infomaniak
This guide explains how…
- … generate a
CSRand private key to request a third-party certificate from a Certification Authority (CA), - … import this certificate for your Infomaniak site, using the
CRTobtained from theCA.
Preamble
- Although Infomaniak offers all the SSL certificates you might need…
- free Let's Encrypt certs for personal sites (only possible with sites hosted at Infomaniak),
- DV certs from Sectigo for professional/private sites that are not registered in the trade register,
- EV certs from Sectigo for companies registered in the trade register,
- It is also possible to install an SSL certificate obtained elsewhere (intermediate certificate from a certification authority of your choice), custom or self-signed certificates.
1. Generate a CSR (Certificate Signing Request)
A CSR (Certificate Signing Request or Certificate Signing Request) is an encoded file containing the information necessary to request an SSL/TLS certificate.
It must be generated on your side to ensure that the private key remains under your control, using for example OpenSSL.
Adapt and run the following command from a terminal application (command line interface, CLI) on your device:
openssl req -utf8 -nodes -sha256 -newkey rsa:2048 -keyout domain.xyz.key -out domain.xyz.csr -addext "subjectAltName = DNS:domain.xyz, DNS:www.domain.xyz"
Explanations
newkey rsa:2048: Generates a new 2048-bit RSA key.keyout domain.xyz.key: Specifies the file where the private key will be saved.out domain.xyz.csr: Specifies the file where the CSR will be saved.addext “subjectAltName = ...”: Adds additional domains via theSAN (Subject Alternative Name)extension, necessary to include all desired domains in the certificate (the main domain domain.xyz + any other associated domain or subdomain, such as www.domain.xyz).
After generation, you can check the contents of the CSR with the following command:
openssl req -in domain.xyz.csr -noout -textThis allows you to verify that all domains listed in subjectAltName are correctly included.
Once the CSR is generated, you can send it to the certification authority (CA) to obtain your SSL/TLS certificate.
2. Import the external certificate
Once validated, the CA issues a certificate (domain.xyz.crt) and sometimes an intermediate certificate (ca_bundle.crt). To access SSL certificate management:
- Click here to access the management of your product on the Infomaniak Manager (need help?).
- Click directly on the name assigned to the relevant product.
- Click on SSL Certificates in the left sidebar.
- Click the blue Install a certificate button:

- Choose the custom certificate.
- Click on the Next button:

- Import your certificate and private key, either by importing the
.crtand.keyfiles or by copy-pasting. - Click on Complete:

Alternative command to generate a self-signed certificate (optional)
If you want a local certificate for testing purposes only or without going through a CA (not recommended for production), you can use this command:
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout domain.xyz.key -out domain.xyz.crt -addext “subjectAltName = DNS:domain.xyz, DNS:www.domain.xyz”This generates both a self-signed certificate (domain.xyz.crt) and a private key (domain.xyz.key). However, self-signed certificates are not recognized as valid by public browsers or systems. They are only suitable for internal or development environments.
Import an intermediate certificate
When adding a custom SSL certificate, it is possible to import the intermediate certificate (by importing the .crt file or pasting the data provided by the certification authority):
This guide details the conditions and procedure for obtaining a Sectigo EV SSL certificate with Infomaniak.
Preamble
- Extended validation (EV) SSL certificates can only be issued to organizations, companies, and firms legally registered with a recognized government authority (such as a commercial register).
- Sectigo and Let's Encrypt DV certificates are not subject to this constraint.
- Compare available SSL certificates
- In case of DV or EV certificate validation issues, refer to this other guide.
EV certificate validation procedure
Obtaining an EV SSL certificate can take up to 24 hours and requires valid information from the client.
This procedure is repeated every 12 months, regardless of the subscription duration chosen for the EV certificate.
1. Verification of company details
The data to be added to the certificate must first be verified with an independent source:
- the legal or commercial name
- the legal form
- the address
- the postal code
- the region / canton / department
- the country / country code
Warning:
- The company name must exactly match the one registered with the commercial register or chamber of commerce; the order can only be processed if the name provided is registered and correctly noted.
- Only the registered legal name or the trademark name followed by the legal name in parentheses is allowed [example: Commercial Name (Legal Name)]; for entities without a legal name, all commercial names can be used.
- It is forbidden to use a postal address.
Given the above, a new request with correct data in the CSR is sometimes necessary, and Infomaniak may also need your approval to make changes to the information provided during the order.
2. Verification of data in the WHOIS directory
The WHOIS directory displays the information of the owner of a domain name. This data must match the information provided when ordering the EV SSL certificate.
To update the information of a domain in the WHOIS:
- If your domain is managed at Infomaniak, refer to this other guide.
- If your domain is not managed at Infomaniak, contact your host/registrar.
3. Contract & validation for the EV certificate
After ordering an EV certificate, the designated company contact person at the time of the order will receive an email from the certification authority Sectigo with the following documents:
- the certificate request form
- the certificate contract
These documents are pre-filled and the contact person must validate them online using an additional code. This will be provided by a Sectigo telephone robot (the call number will come from the Netherlands, +31 88 775 77 77 in principle) orally to your number registered with the registry or the chamber of commerce.
Each certificate request is validated by phone, including renewals and reissues of multi-domain certificates.
For any questions regarding validation, contact Sectigo directly.
4. Domain verification (only for external sites)
This step verifies that you have control of the domain (if it is external to Infomaniak) for which the certificate is requested. Domains of sites hosted at Infomaniak are validated automatically.
Each (sub-)domain must be approved individually via one of the methods described in this other guide.
This guide details the conditions and procedure for using a Sectigo Infomaniak certificate on a site hosted elsewhere, with a third-party host.
Preamble
- You have the possibility to benefit from Infomaniak's advantageous rates for your SSL certificates while managing your sites with another host.
Install a Sectigo certificate
Due to the different providers, the installation of your certificate will not be automatic:
1. Obtain the CSR
Export the CSR configuration file from your host and enter it when ordering your certificate with Infomaniak.
2. Confirm domain ownership
Validate the domains included in the certificate via one of the following methods:
- Enter a validation code received at one of the following email addresses (the full email address must exist on the domain to be validated, here “
domain.xyz” for example):- admin@domain.xyz
- administrator@domain.xyz
- hostmaster@domain.xyz
- postmaster@domain.xyz
- webmaster@domain.xyz
- Creation of a unique CNAME record in the domain's DNS.
- Validation txt file to upload via FTP to your site.
This guide details the validity rules for EV and DV SSL certificates (effective September 1, 2020).
SSL certificate validity period
Following a meeting of the CA/B Forum, which brings together major web players (Safari, Google Chrome, Mozilla Firefox, etc. - learn more), it was decided to set the maximum validity period for SSL certificates to 397 days. This change aims, among other things, to limit the risk of certificate hacking and to increase the security level of certificates. It is not excluded that the maximum validity period of a certificate may be further reduced in the coming years. Some players like Apple, Google, or even Sectigo are pushing in this direction.
The Infomaniak SSL certificates Let's Encrypt are not affected by this change; Infomaniak takes care of everything! The EV and DV certificates from Sectigo issued before August 19, 2020 remain valid, regardless of their duration.
Sectigo SSL DV certificates
Sectigo SSL DV certificates with a duration exceeding 1 year are automatically renewed by Infomaniak (certificate reissued during the month preceding its expiration date).
It is necessary to reinstall the certificate on your site if the latter is not managed by Infomaniak.
Sectigo SSL EV certificates
Sectigo SSL EV certificates will need to be validated each year, regardless of the subscription duration chosen.
It is necessary to reinstall the certificate on your site if the latter is not managed by Infomaniak.
This guide explains how to generate a certificate signing request (CSR) for a domain name and all its subdomains with a Web Hosting (excluding free hosting of type Starter).
This allows you to encrypt the connection to your domain name and all its subdomains via SSL.
Set up a Wildcard certificate
1. Add an alias domain with an asterisk *
To add an alias of type * to your website:
- Click here to access the management of your product on the Infomaniak Manager (need help?).
- Click directly on the name assigned to the product concerned:

- Click on the chevron to expand the Domains section of this site.
- Click on the Add a domain button:

- Enter the domain name to be added in this format:
*.domain.xyz(the asterisk is mandatory, followed by a dot, then the domain name of the website which is domain.xyz in this example)
- Click on the Confirm button to complete the procedure:

2. Install an SSL certificate or update it
Example of updating the existing certificate to include the wildcard subdomain *:
- Click here to access the management of your product on the Infomaniak Manager (need help?).
- Click directly on the name assigned to the product concerned.
- Click on SSL in the left sidebar.
- Click on the action menu ⋮ located on the right.
- Click on Change the certificate:

- Select the same certificate that you already own.
- Click on the Next button:

- Make sure the recently added subdomain is selected.
- Click on the Install button at the bottom:

- Wait for the creation or update to complete.
This guide explains how to add or modify one or more CAA type records in the DNS zone (of a domain name) managed on the Manager Infomaniak.
Introduction
- A CAA record allows you to specify a certification authority authorized to issue certificates for a domain.
Add a CAA
Refer to this other guide to manage this type of record in a DNS zone.
Adding CAA to validate an SSL certificate…
… Sectigo
In the case of a SSL certificate validation for Sectigo, follow the generic guide above but enter the following data specifically:
- Select "Issue for Certification Authority".
- Enter the flag:
0. - Specify
sectigo.com:
… Let's Encrypt
In the case of a SSL certificate validation for Let's Encrypt, follow the generic guide above but enter the following data specifically:
- Select "Issue for Certification Authority".
- Enter the flag:
0. - Specify
letsencrypt.org:
The Sectigo guarantee is a financial commitment from Sectigo, the Certification Authority (CA), aimed at protecting the end user.
It applies only if the user suffers a financial loss due to a validation error by Sectigo when issuing the certificate.
It does not cover security vulnerabilities in your server or misconfigurations on your part.
The higher the validation level (DV < OV < EV), the higher the amount of the Sectigo guarantee is generally.
This guide explains how to uninstall an SSL Certificate regardless of its type, initially installed from the Infomaniak Manager. If your certificate is of the paid type and you wish to cancel the current offer instead, refer to this other guide.
Remove an SSL certificate
To uninstall an Infomaniak certificate:
- Click here to access the management of your SSL certificate on the Infomaniak Manager (need help?).
- Click directly on the name assigned to the product concerned:
- Click on the action menu ⋮ located to the right of the item concerned.
- Click on Uninstall:
- Confirm the uninstallation of the certificate.
This guide explains how to add a dynamic trust seal to a secure site with a SSL certificate from Sectigo.
Preamble
- Infomaniak, as a host, offers SSL certificates to secure its clients' websites
- Sectigo (formerly known as Comodo) is a recognized SSL certificate provider that offers different levels of security
- The "dynamic trust seal", or "Sectigo Trust Seal" / "Sectigo Trust Logo" is a visual that website owners can display on their pages to indicate to visitors that their connection is secure, a sign of trust that informs users that transactions and information exchanges made on the site are encrypted and protected by an SSL certificate issued by Sectigo.
- By using a Sectigo SSL certificate and displaying the dynamic trust seal, a website at Infomaniak benefits not only from data exchange security but also from increased user trust, essential for e-commerce and personal information protection.
Adding a trust seal
Here's how a dynamic trust seal works:
- Validation: to obtain such a seal, the site owner must first obtain a valid SSL certificate from Sectigo, which requires a validation process; depending on the level of certificate chosen (Domain Validation - DV, Organization Validation - OV or Extended Validation - EV), this validation may be more or less in-depth
- Installation: once the SSL certificate is obtained and installed on the Infomaniak web server, the website is then able to establish secure HTTPS connections
- Displaying the seal: Sectigo provides an HTML code or script that the site owner can then integrate into their website; this code allows the Sectigo dynamic trust seal to be displayed
- Update: the seal is often updated in real-time to reflect the current status of the SSL certificate; if the certificate were to expire or be revoked, the seal would also reflect this, warning potential visitors that the site may no longer be secure
The trust seal consists of an image and an HTML code. The latter only works if a Sectigo certificate is installed on the site and in this case generates an interactive logo that displays the certificate data.
Save one of the images below
Right-click on the image to save, then click on Save image as...
- Small

- Medium

- Large

Upload the image to your site
Send the image to your web server (via FTP or your CMS) and note the URL to access this image for the next step (for example https://domain.xyz/wp-content/uploads/sectigo.png).
Get the code to integrate into your pages
Enter the full address of your image on the page https://www.trustlogo.com/install/index2.html to check if the image is accessible.
Click the Continue button on the same page to get the 2 codes to copy-paste into the header of your (or your) web page(s):

Important:
- In the code,
CL1corresponds to aDVSSL certificate; replaceCL1withSC5for anEVtype SSL certificate.
This guide explains how to download or export an SSL certificate from the Infomaniak Manager.
Preamble
- The download of the certificate produces a file in
.zipformat. - The archive contains the
.keyand.crtfiles (as well as_windows.pfx&.protected.keydepending on the type of certificate):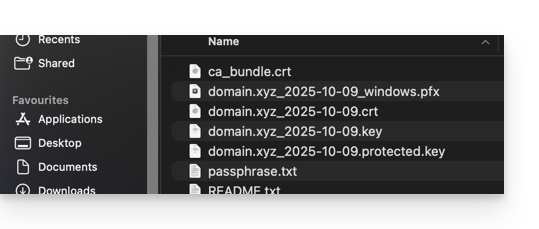
- It is recommended to store this certificate and its private key in a secure location, as the latter could allow access to your encrypted data.
Export or download an SSL certificate
To access the management of your certificates:
- Click here to access the management of your product on the Infomaniak Manager (need help?):
- Filter your certificate types if necessary by clicking on the icon dedicated to this effect.
- Display the different types of certificates such as Let's Encrypt, Sectigo DV & EV...
- Add the certificates that need to be displayed.
- Apply the filters:
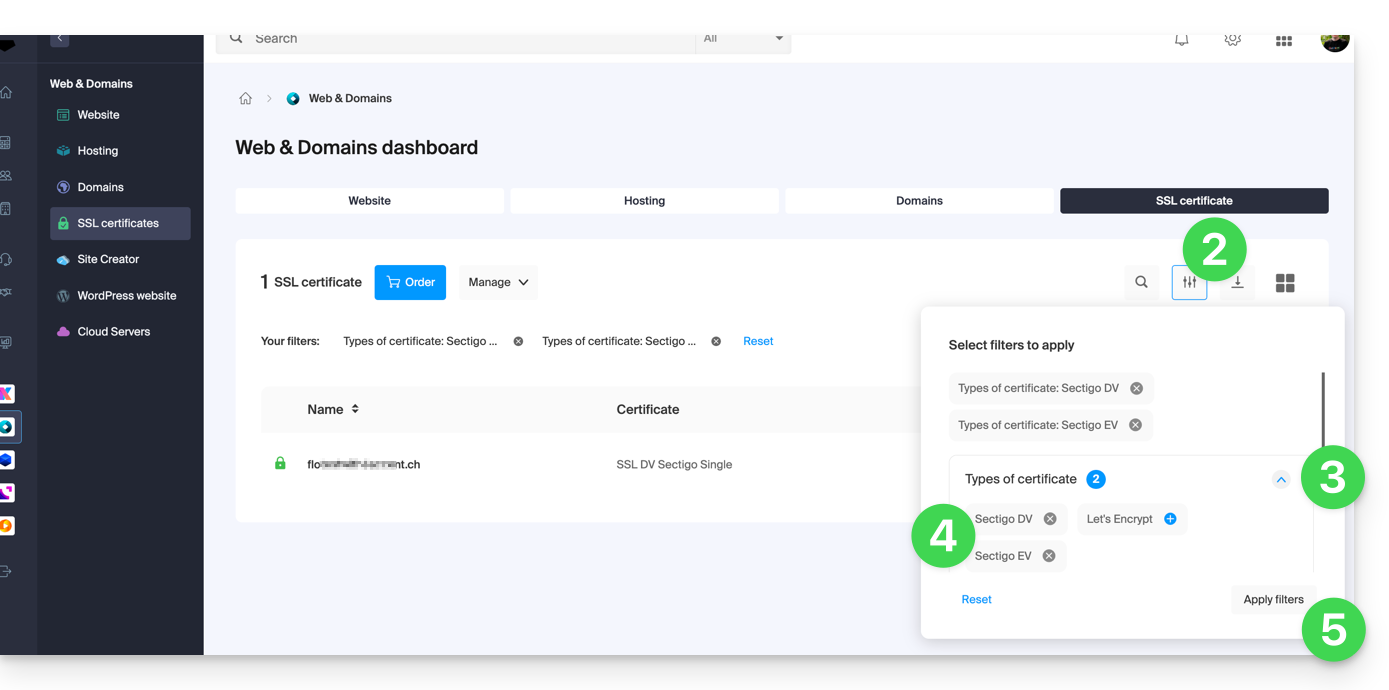
- The table now only displays the types of certificates you have selected.
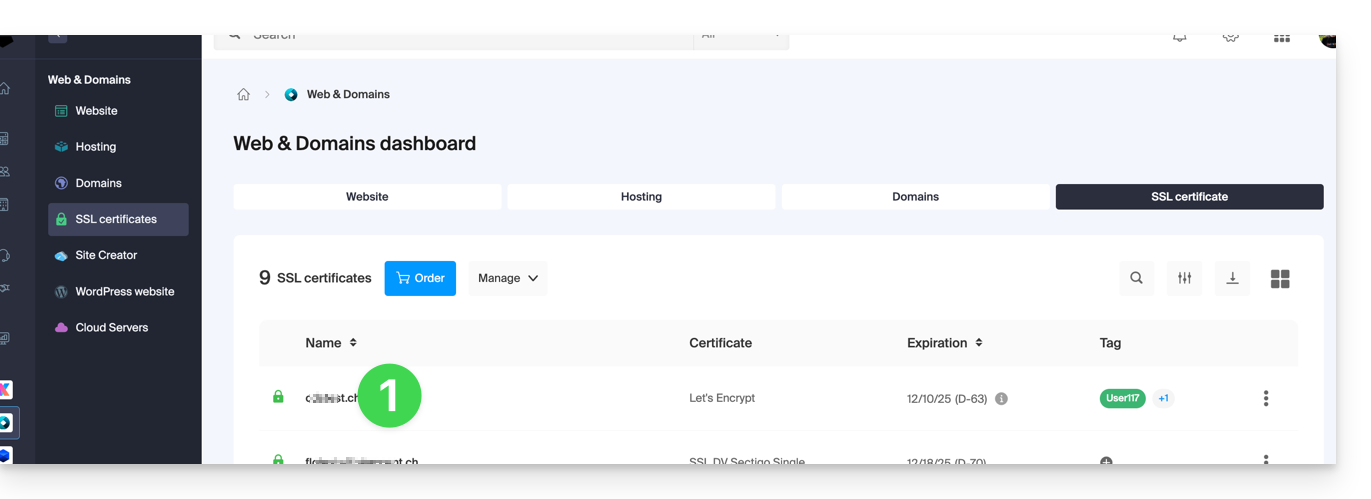
Export a Let's Encrypt certificate
- Click directly on the name assigned to the certificate Let's Encrypt in the list:
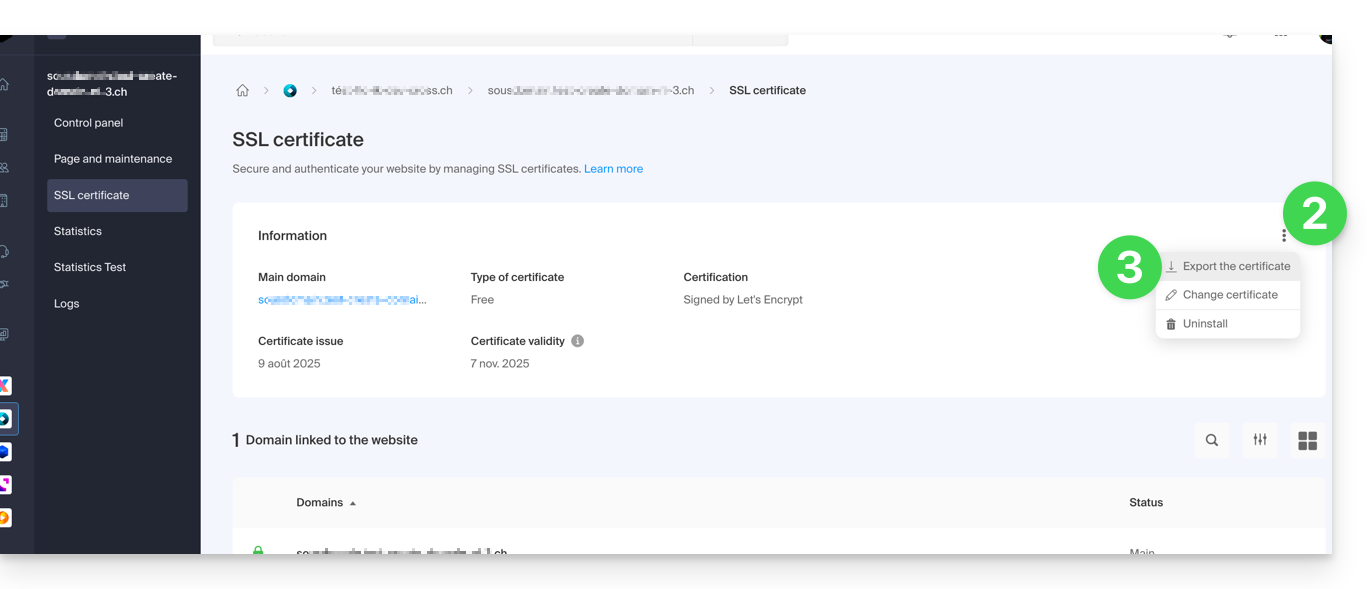
- Click on the action menu ⋮ to the right of the object concerned in the table that appears.
- Choose Export the certificate and follow the instructions to download the archive to your device:
Export a Sectigo certificate
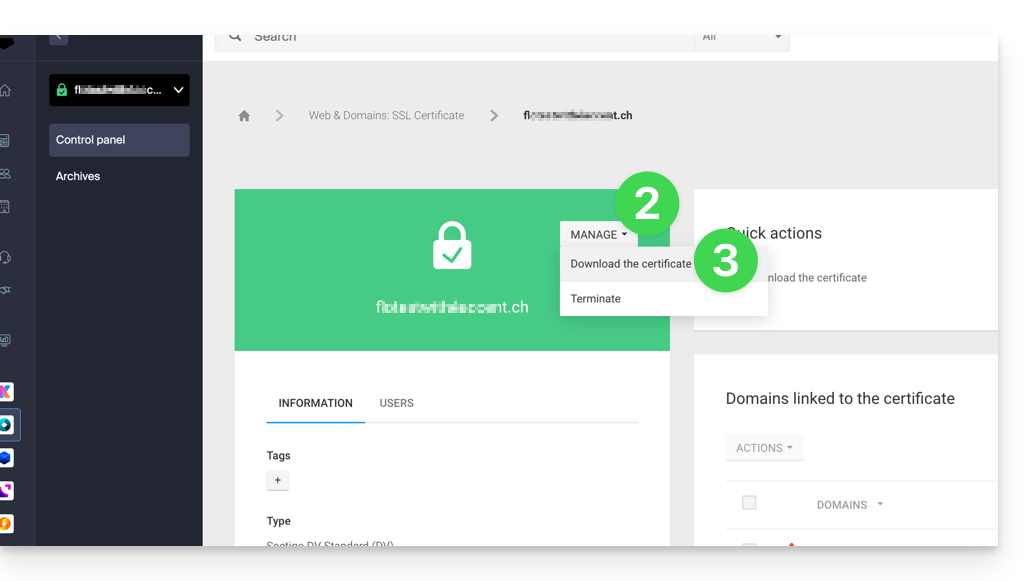
- Click directly on the name assigned to the certificate in the list of certificates.
- Click on the Manage button.
- Click on Download the certificate and follow the instructions to download the archive to your device:
This guide explains how to correctly interpret the detailed information provided by Qualys SSL Labs (https://www.ssllabs.com/ssltest/) which can sometimes seem technical or alarming without the appropriate context.
Preamble
- Qualys SSL Labs is a widely used analysis tool to evaluate the SSL/TLS configuration of websites.
- The warnings in their reports are often just technical details with no impact on the site's security or SEO.
Multiple certificates in SSL Labs reports
When SSL Labs analyzes a site, it may display several numbered certificates (certificate #1, certificate #2, etc.). This happens for several reasons:
- Main certificate (#1): The certificate presented when SNI (Server Name Indication) is used.
- SNI is a TLS extension that allows a server to host multiple SSL certificates for different domains on the same IP address. When a browser connects, it indicates the domain name it wants to join.
- Secondary certificate (#2): The certificate presented when SNI is not used or during a direct IP connection.
An indication "No SNI" in certificate #2 is not an error. It simply means that SSL Labs has tested what happens when a client connects without providing SNI information. In this case:
- The server provides a fallback certificate (often a generic or preview certificate).
- This situation only affects very outdated clients that do not support SNI.
- Modern browsers all use SNI and will therefore receive certificate #1.
Certificate chain issues
Chain issues: Incorrect order, Extra certs, Contains anchor
These warnings do not necessarily mean that the certificate is defective:
Incorrect order: Intermediate certificates are not presented in the optimal order.Extra certs: Unnecessary additional certificates are included.Contains anchor: The root certificate is included in the chain.
The TLS protocol allows omitting the root certificate as it is normally already present in the browsers' certificate stores. Including it is not an error, but a redundancy.
Alternative names mismatch
For the rescue certificate (#2), the "MISMATCH" warning is normal because:
- This certificate is designed for another domain (
preview.infomaniak.website). - It is only presented when SNI is not used.
- The browser receiving this certificate would identify it as not matching the requested domain, but this does not affect normal connections with SNI.
Regarding SEO concerns:
- Google and other search engines use modern browsers that support SNI.
- They receive certificate #1, which is valid for your domain.
- Warnings about certificate #2 have no impact on SEO.
- Only issues with the main certificate (#1) could affect SEO.
This configuration is perfectly suited for shared hosting where multiple sites share the same infrastructure, with a preview certificate serving as a fallback solution.
This guide explains how to obtain a type of SSL certificate .p12 2048 bits , useful in particular for SAP, Salesforce, etc. from the Infomaniak infrastructure.
Obtain a p.12 type certificate
A p.12 type certificate is a container that includes the certificate, intermediate CAs, and the key itself.
It is possible to create this type of certificate from what can be downloaded from the Infomaniak Manager:
- Order a certificate for the domain
sap.domain.xyzby providing a CSR (which means having the private key, named for exampleserver.key) - Download the certificate generated in the Infomaniak Manager:
sap.domain.xyz-15-03-2024.zip - Unzip the archive
Run this:
openssl pkcs12 -export -out server.p12 -inkey server.key -in sap.domain.xyz.crt -certfile ca_bundle.crt
A file server.p12 will then be obtained.
If the certificate was generated without a CSR, it is the file .key present in the downloaded zip that will serve as the key.
This guide is for you if you are experiencing issues with a Sectigo SSL certificate of type DV or EV.
Sectigo Change (June 2025)
Since June 2025, Sectigo uses a new validation infrastructure called MPIC, which performs the necessary checks to issue SSL certificates (including EV and OV) from servers located around the world, and no longer solely from the United States.
A challenge is a method used by the certification authority to verify that the applicant controls the domain. This can be done through an HTTP request, a DNS record, or an email. For EV and OV certificates, this challenge is combined with checks on the organization's identity.
With this new method, validation requests can come from any country or provider. If your site or server uses geoblocking rules, a web application firewall (WAF), or a service like Cloudflare with country or ASN access restrictions, these checks may be blocked, causing validation to fail.
Even though Sectigo primarily discusses OV and EV certificates, this change can also indirectly affect DV certificates, as domain validation still relies on the ability to access the necessary resources.
⚠️ To avoid any issues, it is recommended to temporarily disable any geographical restrictions or network filtering during certificate validation.
This guide explains how to add two different EV or DV SSL Certificates to the same site.
Preamble
- Since it is not possible to install two SSL certificates on the same site, it is necessary to create two identical sites.
Creation of the second site
Prerequisites
- Remove any potential alias domain name from your site.
To access the Web Hosting to add a site:
- Click here to access the management of your product on the Infomaniak Manager (need help?).
- Click directly on the name assigned to the product in question.
- Click on the button Add a site:
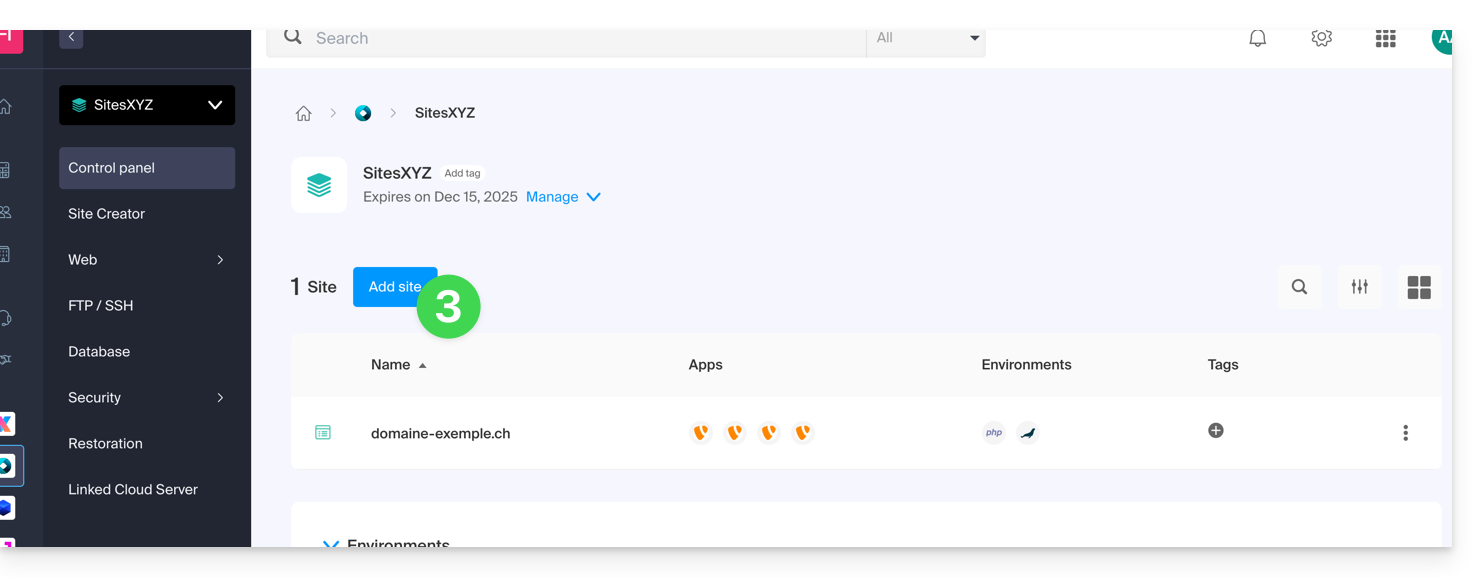
- Continue without installing a tool:
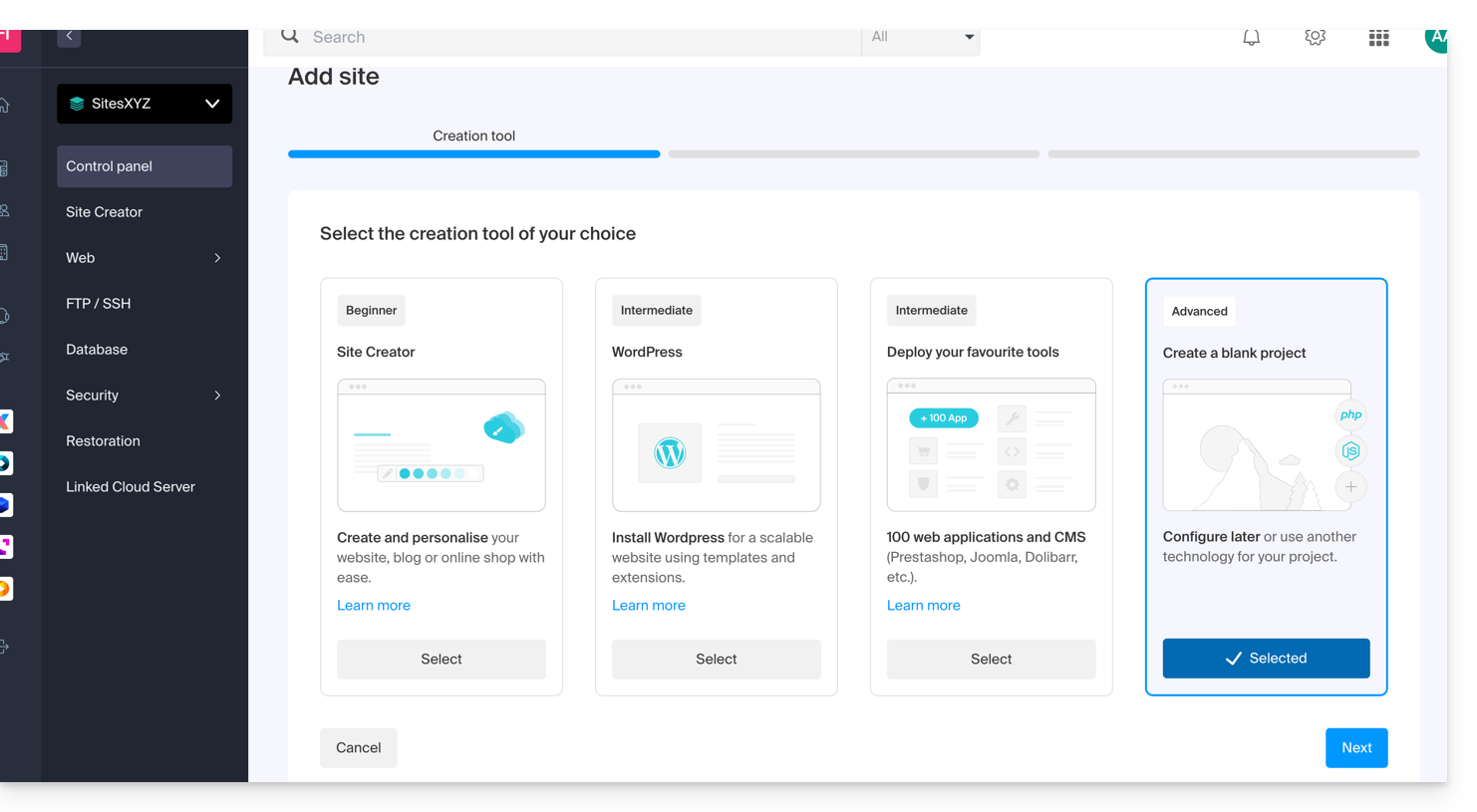
- Click on Apache and choose the same PHP version as the main site::
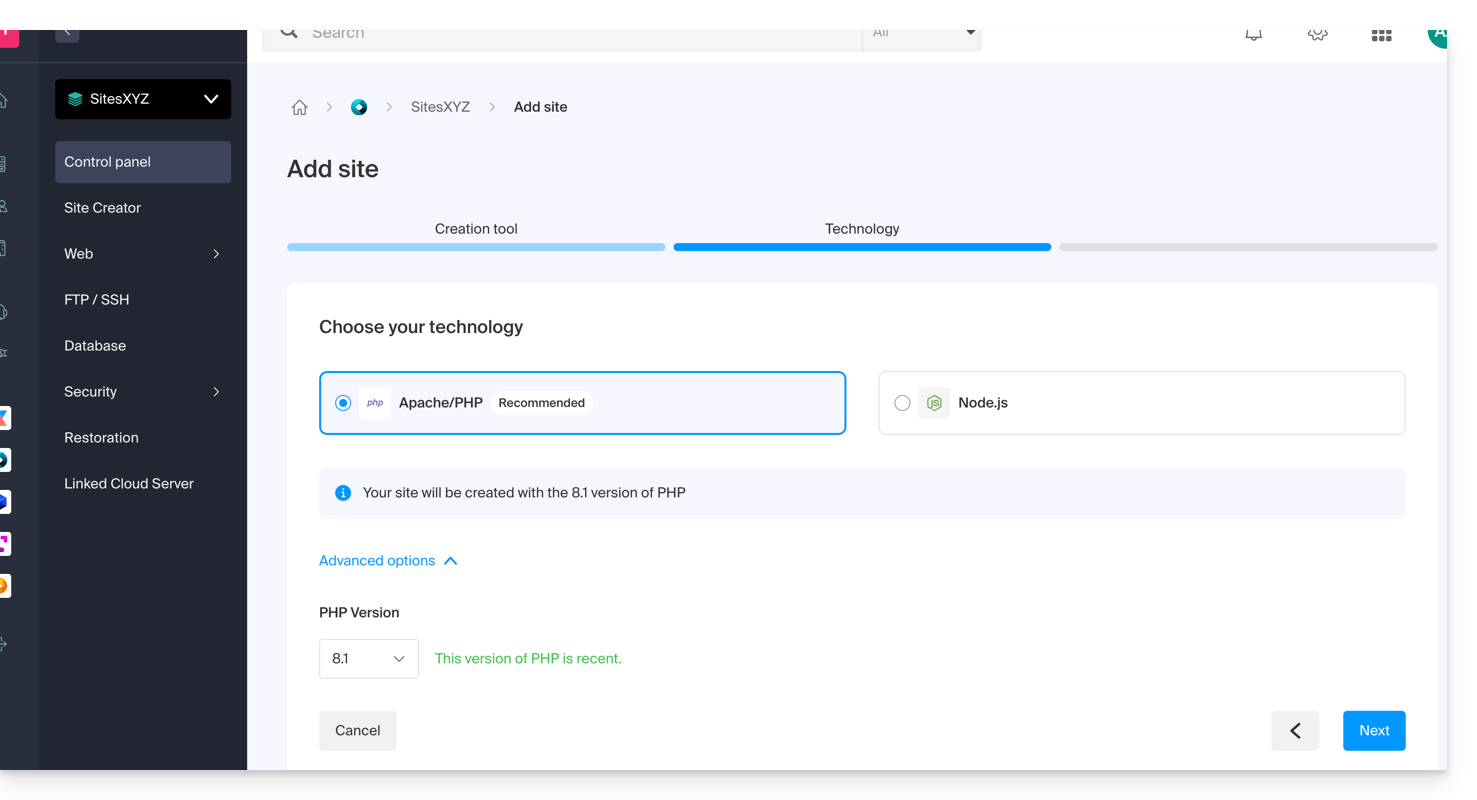
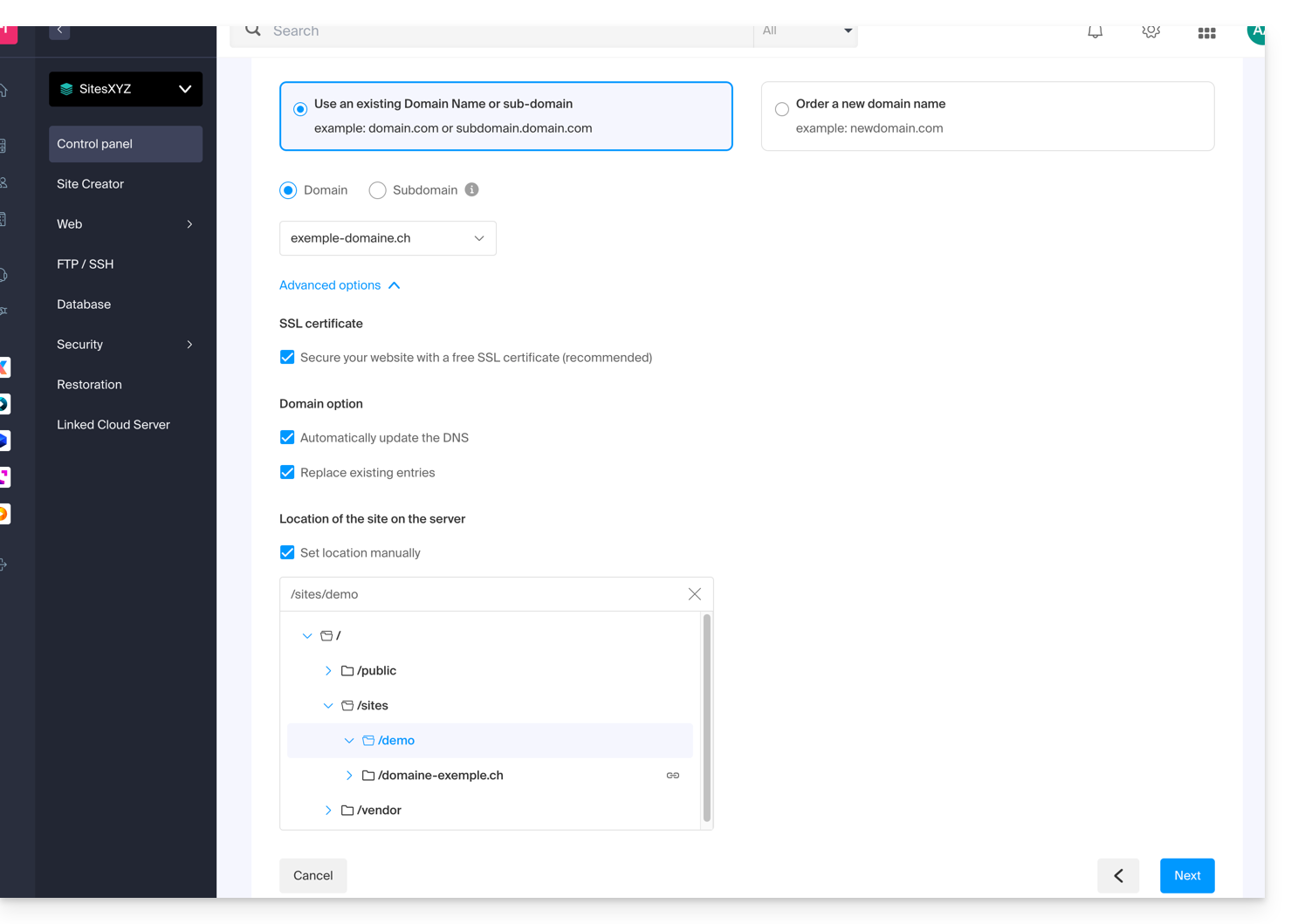
- Choose between using a domain name or a subdomain.
- Enter the domain or subdomain name.
- Click on Advanced options.
- Activate (or not) the Let's Encrypt SSL certificate on the future site.
- Check the box Manually define the location.
- Choose the same location as the main site:
- Click on the blue button Next to start the site creation.
Install the SSL certificate
Once the second site is created (any addition/modification can take up to 48 hours to propagate), you will be able to install an SSL certificate (if you chose not to install the certificate in step 9 above).
To access website management:
- Click here to access the management of your product on the Infomaniak Manager (need help?).
- Click directly on the name assigned to the product in question.
- Click on SSL Certificates in the left sidebar.
- Click on the blue button Install an SSL certificate and follow the procedure.

