1000 FAQs, 500 tutorials and explanatory videos. Here, there are only solutions!
Secure a video stream with a unique key
This guide explains how to restrict access to Infomaniak's Video Streaming streams using a unique key (hash).
Preamble
- This method offers the highest level of protection and allows you to restrict your broadcasts to a member area that requires authentication, for example.
- Since the way to generate this code is specific to each site, it will be necessary to implement the required PHP functions and adapt the integration code of your player accordingly.
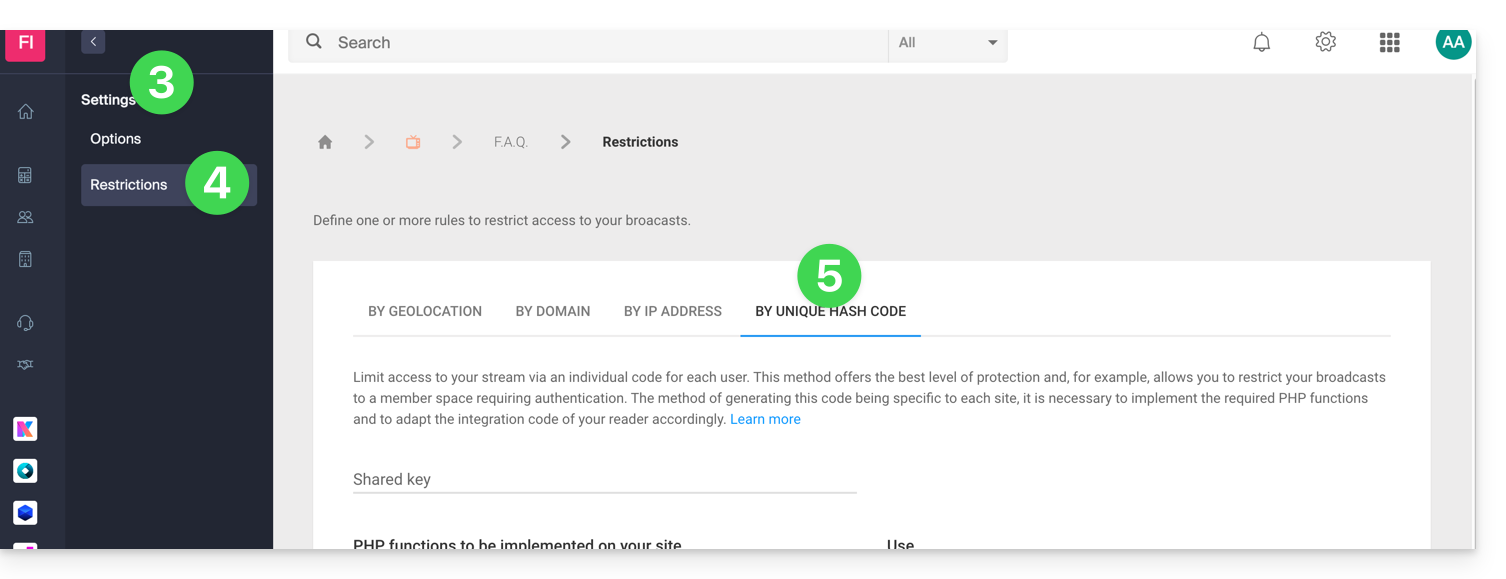
Restrict access to broadcasts by unique key (hash)
To do this:
- Click here to access the management of your product on the Infomaniak Manager (need help?).
- Click directly on the name assigned to the product in question.
- Click on Settings in the left sidebar.
- Click on Restrictions in the left sidebar.
- Click on the tab (or dropdown menu item) Unique hash restriction:
How restrictions work
This method requires retrieving information related to the configuration of your stream and the viewer who is connecting.
First, you need to create a password (a key) in the Infomaniak Manager. As soon as this key is added, connected viewers and those attempting to view your stream will be instantly blocked (refer to this other guide to customize the replacement image offered to blocked viewers).
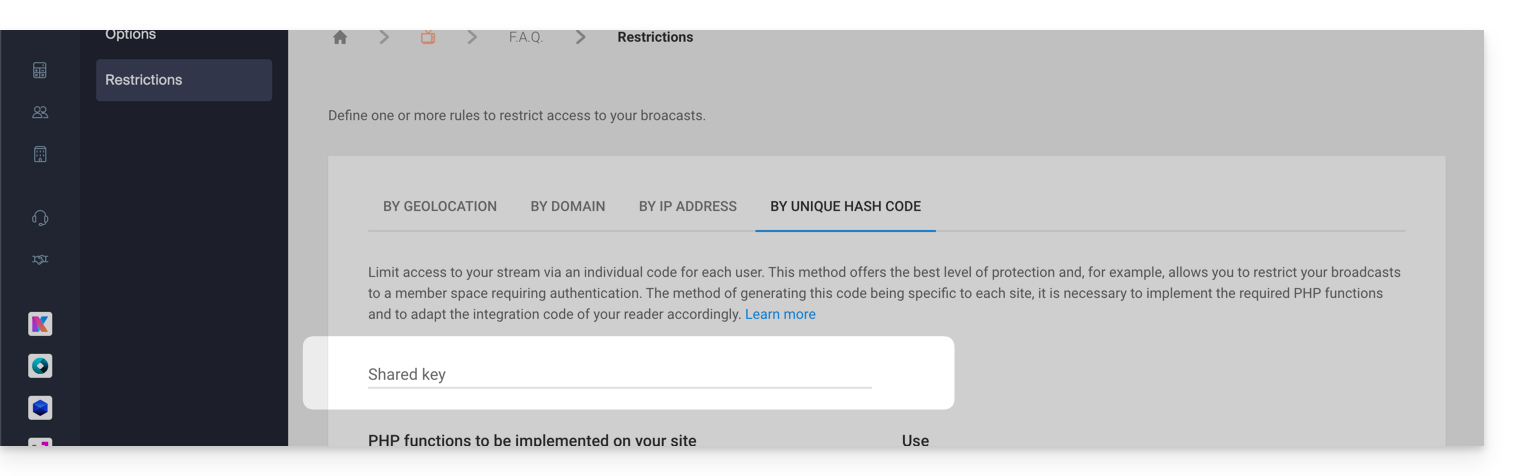
Here is the principle to follow to authorize access to your stream:
- Designing an authentication system by yourself (e.g., a member area).
- Retrieve the password configured above in the Manager.
- Retrieve the IP addresses of users via
$_SERVER["REMOTE_ADDR"]for example. - Retrieve the identifier of the stream to target.
- Retrieve the current date and time (without minutes and seconds).
These elements will then be hashed by the code provided in the Manager to generate a unique token for each user, which will be transmitted to the stream at the time of its loading. The streaming platform will then check the validity of the hash to authorize or reject the connection.
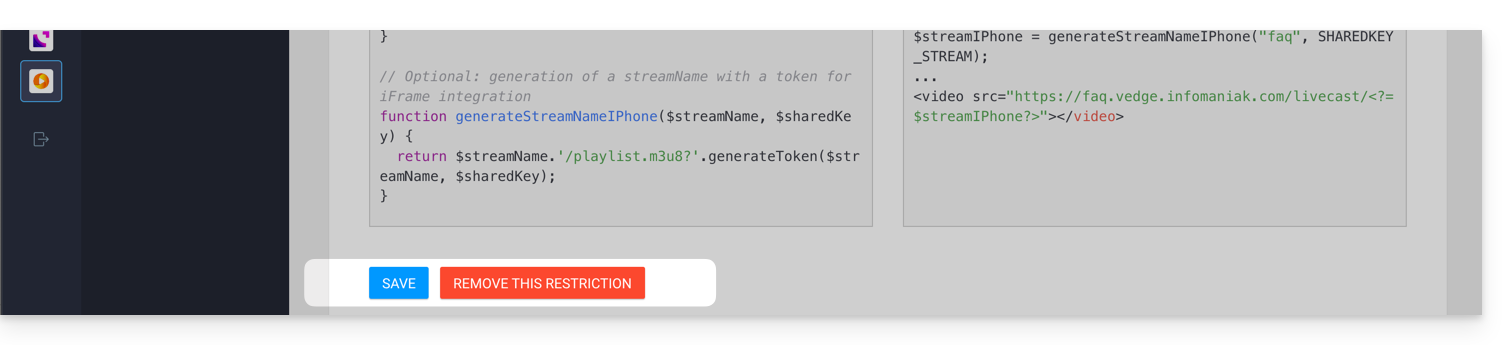
Important notes
- To ensure the security of access to the stream, the validity of each token is time-limited.
- It is important to disable the cache on the pages that allow access to the stream; indeed, if the token generation is cached, other users will attempt to authenticate with someone else's hash, which will result in their rejection even if they are authorized to consume the stream.

